Phishing Attack Simulation & Security Awareness Training Platform
About
Prepare your organization for cyber threats with the Advanced Attack Simulation Training Platform. Test defenses, train personnel, and identify vulnerabilities safely. Boost security with realistic simulations, tailor made training programs and appropriate response practices.


Attack Simulation & Phishing Campaign Manager Module
Phishing Manager Profiles
The feature allows the Phishing Manager to set up various sender identities for simulated Phishing emails, enabling diverse and realistic scenarios to test user vulnerability.
Onboard Users
This feature enables adding new users to the platform, assigning them to groups, and managing their participation in both Phishing simulations and training programs.
Phishing Email Template Builder
A tool that facilitates the creation of custom Phishing email templates, allowing administrators to design the email's subject, body, and attachments to mimic actual Phishing attacks.
Pre-Built Phishing Email Template
Provides access to a comprehensive library of pre-designed Phishing email templates, crafted to resemble real Phishing attacks, for immediate use in simulations.
Build & Run Campaigns
Admins can design, schedule, and run phishing simulations, choosing targets, attack types, and email timing.
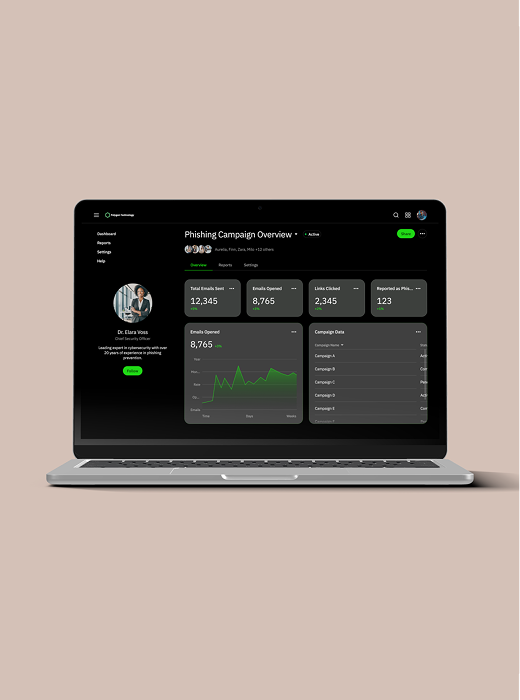
Campaign Insights & Reporting
Offers detailed analytics and reports on user responses to Phishing simulation campaigns, including click rates, response times, and user actions, to evaluate training effectiveness.
Phishing Manager profiles
The feature allows the Phishing Manager to set up various sender identities for simulated Phishing emails, enabling diverse and realistic scenarios to test user vulnerability.
Onboard Users
This feature enables adding new users to the platform, assigning them to groups, and managing their participation in both Phishing simulations and training programs.
Phishing Email Template Builder
A tool that facilitates the creation of custom Phishing email templates, allowing administrators to design the email's subject, body, and attachments to mimic actual Phishing attacks.
Pre-Built Phishing Email Template
Provides access to a comprehensive library of pre-designed Phishing email templates, crafted to resemble real Phishing attacks, for immediate use in simulations.
Build & Run Campaigns
Admins can design, schedule, and run phishing simulations, choosing targets, attack types, and email timing.
Campaign Insights & Reporting
Offers detailed analytics and reports on user responses to Phishing simulation campaigns, including click rates, response times, and user actions, to evaluate training effectiveness.
Phishing Manager profiles
The feature allows the Phishing Manager to set up various sender identities for simulated Phishing emails, enabling diverse and realistic scenarios to test user vulnerability.
Onboard Users
This feature enables adding new users to the platform, assigning them to groups, and managing their participation in both Phishing simulations and training programs.
Phishing Email Template Builder
A tool that facilitates the creation of custom Phishing email templates, allowing administrators to design the email's subject, body, and attachments to mimic actual Phishing attacks.
Pre-Built Phishing Email Template
Provides access to a comprehensive library of pre-designed Phishing email templates, crafted to resemble real Phishing attacks, for immediate use in simulations.
Build & Run Campaigns
Admins can design, schedule, and run phishing simulations, choosing targets, attack types, and email timing.
Campaign Insights & Reporting
Offers detailed analytics and reports on user responses to Phishing simulation campaigns, including click rates, response times, and user actions, to evaluate training effectiveness.
Training Module
Create Training Programs
Allows administrators to craft detailed educational content, including videos, slides, and texts, to educate users on recognizing and responding to Phishing attacks.
Assign Training Programs
Admins can assign tailored training programs to users or groups, aligning content with their roles and needs.
Interactive Quizzes
Includes interactive quizzes that test users' understanding of key cybersecurity concepts, presenting real-world scenarios and questions to reinforce learning and improve retention.
Track Progress
Allows tracking of user progress through training programs, including completion status, quiz scores, and engagement levels, to ensure training effectiveness.
Earn Certification
Upon completing training programs, users receive certifications recognizing their proficiency in cybersecurity best practices, valuable for compliance and personal records.
Create Training Programs
Allows administrators to craft detailed educational content, including videos, slides, and texts, to educate users on recognizing and responding to Phishing attacks.
Assign Training Programs
Admins can assign tailored training programs to users or groups, aligning content with their roles and needs.
Interactive Quizzes
Includes interactive quizzes that test users' understanding of key cybersecurity concepts, presenting real-world scenarios and questions to reinforce learning and improve retention.
Track Progress
Allows tracking of user progress through training programs, including completion status, quiz scores, and engagement levels, to ensure training effectiveness.
Earn Certification
Upon completing training programs, users receive certifications recognizing their proficiency in cybersecurity best practices, valuable for compliance and personal records.
Create Training Programs
Allows administrators to craft detailed educational content, including videos, slides, and texts, to educate users on recognizing and responding to Phishing attacks.
Assign Training Programs
Admins can assign tailored training programs to users or groups, aligning content with their roles and needs.
Interactive Quizzes
Includes interactive quizzes that test users' understanding of key cybersecurity concepts, presenting real-world scenarios and questions to reinforce learning and improve retention.
Track Progress
Allows tracking of user progress through training programs, including completion status, quiz scores, and engagement levels, to ensure training effectiveness.
Earn Certification
Upon completing training programs, users receive certifications recognizing their proficiency in cybersecurity best practices, valuable for compliance and personal records.
What Sets Polygon Apart?
Flexible Deployment Options
Allows administrators to craft detailed educational content, including videos, slides, and texts, to educate users on recognizing and responding to Phishing attacks.
Adaptive Training Programs
Create customized training programs based on the outcomes of your Phishing simulation campaigns to target specific user weaknesses.
Real-World Phishing Templates
Access a collection of pre-designed Phishing email templates, each based on real-life scenarios, to conduct realistic training simulations.
Flexible Deployment Options
Allows administrators to craft detailed educational content, including videos, slides, and texts, to educate users on recognizing and responding to Phishing attacks.
Adaptive Training Programs
Create customized training programs based on the outcomes of your Phishing simulation campaigns to target specific user weaknesses.
Real-World Phishing Templates
Access a collection of pre-designed Phishing email templates, each based on real-life scenarios, to conduct realistic training simulations.
Flexible Deployment Options
Allows administrators to craft detailed educational content, including videos, slides, and texts, to educate users on recognizing and responding to Phishing attacks.
Adaptive Training Programs
Create customized training programs based on the outcomes of your Phishing simulation campaigns to target specific user weaknesses.
Real-World Phishing Templates
Access a collection of pre-designed Phishing email templates, each based on real-life scenarios, to conduct realistic training simulations.