
Why Employees Are Seen as the Weakest Link in Cyber Security?
Why Employees Are Seen as the Weakest Link in Cyber Security?

Ashfat Al Rashid
SQA Engineer specializing in backend testing, API automation (RestAssured, Postman), and test automation with Java. Proficient in UI automation (Selenium, POM) and performance testing (JMeter). Experienced in manual, regression, database, and UAT testing, ensuring software quality across various platforms.

Md. Asad Chowdhury Dipu

For years, cybersecurity leaders have repeated the mantra: “Employees are the Weakest link”
Statistically, yes — According to Verizon, Data Breach Investigations Report (DBIR) 2023, 74% data breaches happen due to human error. But strategically, this narrative is incomplete and, in many cases, misleading.
But this narrative is focused on blame, not the fix. It highlights human mistakes, not organizational failures. Ignoring the fact that employees are not inherently malicious all the time, which is also backed by well researched stats. They’re simply the most accessible attack surface, shaped heavily by complicated systems, work culture, lack of leadership and workload. The human risk factor could be reduced by 85% according to KnowBe4, Phishing by Industry Benchmarking Report 2025.
In this blog we break down the real reason behind human-driven breaches and what organizations must fix to transform employees from a vulnerability into their strongest line of defense.
The Cybersecurity Pillars: Technology, Processes, People
Cybersecurity professionals rests on the three pillars operational framework:
Technology
Firewalls, endpoint security, intrusion detection, encryption — essential, but insufficient without human alignment. Tools fail when misconfigured, ignored, or poorly integrated.
Processes
Policies, protocols, and structured response mechanisms. They define how technology is used and how incidents are handled. Weak processes amplify human error.
People
Unlike technology or procedures, people act with intention, emotion, fatigue, stress, and free will. But human error usually results from cognitive overload, unclear systems, poor design, or inadequate leadership, not incompetence.
This foundational three-pillar view highlights precisely why the “weakest link” mantra is strategically flawed and outdated. The error is not that the People pillar exists, but that we incorrectly treat it in isolation.
The Strategic Shift is Investing in the People Pillar. The success statistics are undeniable: the global Phish-Prone Percentage drops from an average baseline of over 33% to just 4.1% when training is done right, according to the KnowBe4 Phishing by Industry Benchmarking Report 2025. This is a measurable 85% reduction in risk
So Why Do Humans Become the “Weakest Link”?
While humans are involved in roughly 74% of breaches, the deeper reason is not human nature, it’s the ecosystem humans operate in. Here are the true factors.
Phishing & Social Engineering
Social engineering is the exploitation of human trust, urgency, and authority cues. Modern day attackers use sophisticated, personalized, and psychologically engineered social engineering to make targets click a phishing link . And, still remains one of the most popular yet effective cyber threats to an organization not because employees are careless, but because attackers exploit predictable cognitive triggers.
Cognitive Biase
People may fall for authority bias, urgency and sometimes even overconfidence. There are 30 human factors that research has identified (eg. stress, age, workload, personality, fatigue) which influences vulnerability, and attackers take advantage of these traits.
Behavioral Vulnerabilities
These behaviors stem from practicality, not malice:
- Weak or reused passwords
- Forgetting to verify requests
- Clicking links quickly under pressure
- Acting on autopilot during high workload
One notable study found that 22% of employees who clicked a phishing link didn’t even recall doing so, highlighting how frequently security failures stem from distraction, not intent.
Organizational & Environmental Pressure
Security mistakes rarely come from ignorance they come from overload:
- High workload
- Multitasking
- Fatigue
- Constant context switching
- Tight deadlines
Beauceron Security reports that roughly 40% of phishing clicks occur when people are rushed or distracted. Humans fail when environments force them to operate in high-cognitive-load conditions.
Psychological Safety & Fear
One of the most overlooked vulnerabilities: Employees fear admitting mistakes.
When staff are afraid of punishment:
- Phishing clicks go unreported
- Incidents stay hidden
- Response time increases
- Damage multiplies
A “just culture” dramatically increases reporting, reduces damage, and accelerates containment.
Data Mishandling & Shadow IT
Sending sensitive files to the wrong person, using personal devices, installing unapproved apps usually done for speed or convenience. Shadow IT expands the attack surface and bypasses central security controls.
Weak Security Hygiene
Factors such as:
- Unpatched systems
- Ignoring updates
- Poor password practices
- Unsafe networks
These are process failures as much as human failures.
What the Data Actually Says
Industry reports consistently reveal the human link:
- According to Verizon DBIR 2023, 74% of breaches involve a human element (including error, privilege misuse, stolen credentials, and social engineering).
- Proofpoint’s 2025 Data Security Landscape Report revealed that nearly six in ten (58%) organizations attribute their most significant data loss events to careless employees (negligent insiders), while 32% point to malicious insiders.
- IBM’s Cost of a Data Breach Report 2024 revealed that Phishing-related breaches cost an average of $4.88 million—the highest cost among all initial attack vectors that year.
- Data consistently shows younger generations are more susceptible to certain types of scams: for instance, Millennials and Gen Z are statistically 5x more likely to report a loss on a job scam compared to older adults (Federal Trade Commission, 2022). This highlights a specific vulnerability that cuts across generations.
The Takeaway:
Employees are not the threat exploitation of human behavior is.
Culture, Leadership, and Policy
Cybersecurity is not only a technological function, it’s a cultural one.
1. Security Leadership Matters
Executives who treat security as a shared organizational duty build stronger, more resilient teams. If leaders view security as “IT’s job,” employees will too.
2. Continuous, Role/Personality Based Exercise
One-time annual modules don’t work. High-performing organizations deliver:
- Frequent micro-learning
- Real-world phishing simulations
- Role or personality based exercises
- Scenario-based exercises
- Clear, contextual guidance
Studies show continuous learning & awarness reduces phishing success by up to 86%.
3. Clear, Simple, Actionable Policies
People do not and can not follow what they do not understand, that’s why Policies should be
- Short
- Clear
- Practical
- Supported by enforcement and tooling
- Embedded into daily workflows
4. Implementing A No Blame Culture
Organizational security improves dramatically, when employees feel safe reporting suspicious activities rather than remaining silent out of fear or worrying they’ll be blamed or punished.
5. Rewarding Secure Behaviors
Integrating gamified training exercises, alongside rewarding and providing recognition for secure practices empowers workforces to build positive and secure behaviors quickly.
How to build “The Human Centric Security Model”?
Organizations should practice threat migitigration strategies in a human centric manner in order to establish a strong security culture
1. Strong Authentication & Access Control
- Enforcing MFA everywhere
- Using password managers
- Patch aggressively
- Implementing an automatic malicious email filter
2. Monitoring & Incident Response
- Implementing DLP (Data loss prevention) solutions
- Automated anomaly detection
- Fast containment and remediation
3. Training as a “Habit,” Not an Event
- Microlearning
- Phishing Simulations
- Instant Feedback
- Behavioral Nudges
4. Onboarding & Offboarding Discipline
Removal of access prevents insider misuse and accidental exposure
5. Insider Threat Management
Monitoring high-risk roles are essential.
6. Build Psychological Safety
Make it normal to say:
“I clicked something suspicious. What should I do?”
This single shift can prevent catastrophic breaches.
Implementing this six-point Human-Centric Security Model requires more than technical enforcement; it demands a strategic shift where security is treated as an integrated habit, not an isolated task. The greatest leverage in this model lies in moving Training from an event to a habit and fostering Psychological Safety. This is where organizations struggle with generic tools.
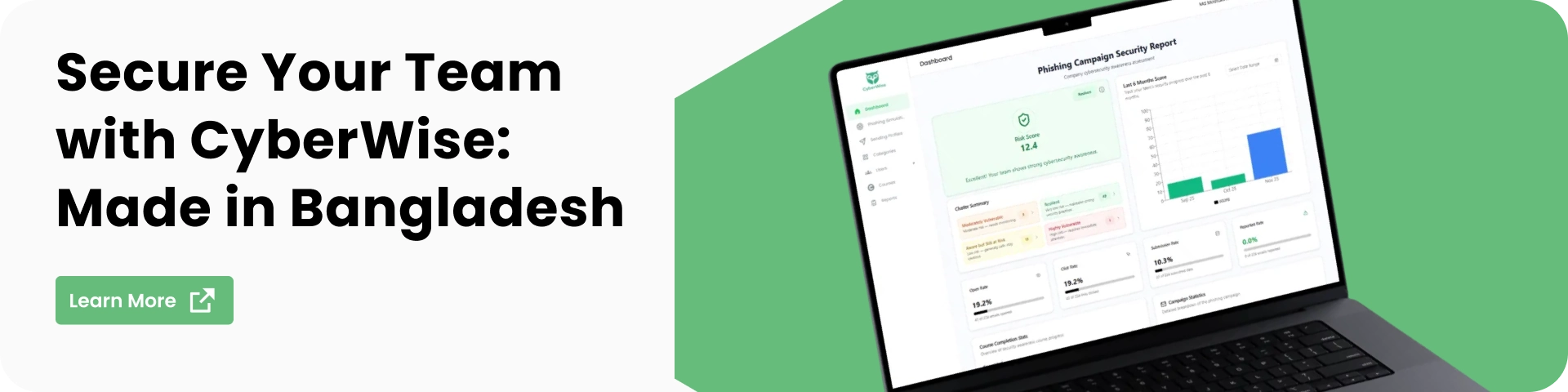
Transforming the Human Element With CyberWise
While statistics confirm that the human element is mostly involved in breaches, making employees the most frequently exploited entry point, viewing them merely as the “weakest link” is strategically flawed. The root cause of these errors often lies in systemic organizational failures, including inadequate exercises, high cognitive load, and flawed processes. An organization’s vulnerability is not really its workforce, but the lack of a human-centric security framework.
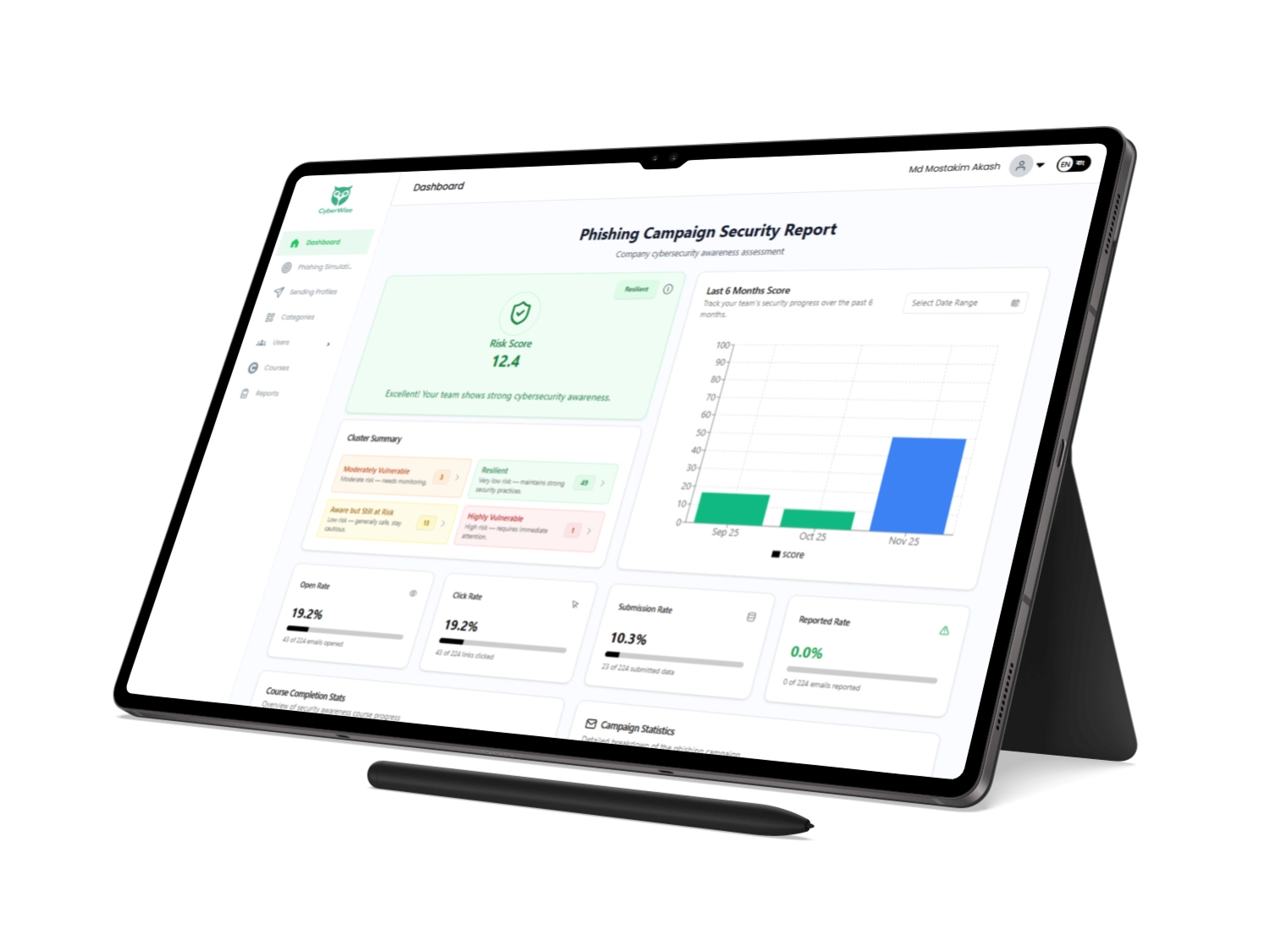
- Realistic Exposure with real world phishing simulations
- Assign tailored Training Programs and Interactive Quizzes to turn simulation failures into immediate, context-specific learning moments.
- The Campaign Insights & Reporting module tracks user progress and knowledge retention, giving you the verifiable data you need to prove your workforce is your strongest line of defense.
Conclusion
JMeter is a powerful tool for any SQA engineer looking to ensure their applications can handle real-world traffic. Whether you’re testing a web application or a backend service, it provides the flexibility to simulate hundreds or even thousands of users. My journey with JMeter has helped me identify bottlenecks, tune system performance, and ensure our applications remain robust under heavy loads.
If you’re new to load testing, don’t worry—JMeter is beginner-friendly but grows with you as you become more proficient. So give it a try and happy testing!